INFORMATION OPERATIONS: ORIGINS AND FUNDAMENTALS - PART II
Sections
Introduction
Taxonomy of IW Forms
Information Infrastructures and Environments
Information Superiority
Importance of Definitions
IW vis-a-vis IO
IW vis-a-vis NCW
The Indian Security Scenario – Overview of IW Status
References
Introduction
Information Warfare (IW) is expected to play an increasingly dominant role in twenty first century conflict, wherein military superiority is a composite function of combat, electronic and information superiority. In this Information Age, we have for the first time the capability to intercept, analyse and disseminate information in real time, with the potential to wage war in the information dimension in powerful new ways. At this juncture, IW appears to have the potential of becoming the dominant rather than a supplementary form of warfare. Various armies are continuously evolving their concepts, doctrines and roadmaps for operationalising Information Operations (IO, a term often used synonymously with IW; more on this has been stated subsequently in this text). This two-part write-up attempts to introduce the concept of IW/ IO, with a view to discussing its applicability and importance in 21st Century warfare in subsequent posts.
In the first part, the fact that the battle for information has been at the core of military operations throughout the ages was first highlighted. Thereafter, the idea of three “waves” of warfare proposed the futurists Alvin and Heidi Toffler was touched upon. The write-up then dwelt on certain theoretical underpinnings of IW, such as a Cognitive Hierarchy, an Information Model of Warfare and the notion of an Information Battlespace.
This discussion is now carried forward here in Part II of the write-up, wherein some well-accepted IW taxonomies are first given out, followed by a brief overview of the notion of Information Superiority. Finally, some comments are made on the status of IW in the Indian context.
Taxonomy of IW Forms
While several IW taxonomies exist, two of the more popular ones are briefly described below.
RAND authors John Arquilla and David Ronfeldt, in their think piece “Cyberwar is Coming!” [1], have distinguished four basic categories of IW in increasing level of intensity, as under:-
- Net Warfare (or Netwar). This war form is information-related conflict waged against nation states or societies at the highest level, with the objective of disrupting, damaging or modifying what the target population knows about itself or the world around it. The weapons of netwar include diplomacy, propaganda and psychological campaigns, political and cultural subversion, deception or interference with the local media, infiltration of computer databases, etc.
- Political Warfare. Political power, exerted by institution of national policy, diplomacy, and threats to move to more intensive war forms, is the basis of political warfare between national governments.
- Economic Warfare. Conflict that targets economic performance by influencing economic factors (trade, technology, trust) of a nation intensifies political warfare to a more tangible level.
- Cyber War. The most intense level is conflict by military operations that target the opponent’s military command and control.
As per Martin Libicki [2], there are seven distinct forms of IW, as under:-
- Command and Control Warfare (C2W). Attacks on command and control systems to separate command from forces.
- Intelligence-Based Warfare (IBW). The collection, exploitation and protection of information to support attacks in other warfare forms.
- Electronic Warfare (EW). Communications combat in the realms of physical transfer of information (electronic) and abstract formats of information (cryptographic).
- Psychological Warfare (Psy W). Combat against the human mind.
- Hacker Warfare (Hacker W). Combat at all levels over the global infrastructure.
- Economic IW (EIW). Control of economics via control of information by blockade of imperialistic controls.
- Cyber Warfare (Cyber W). A combination of futuristic abstract forms of terrorism, fully simulated combat and reality control.
Libicki further states that all these forms are weakly related and lack analytical coherence.
Information Infrastructures and Environments
Information, the predominant target of IW, either is resident in or flows over Global, National or Defence Information Infrastructures (GII, NII and DII) [3]. These in turn serve the information needs of individuals, organisations and systems comprising the Global and Military Information Environments (GIE and MIE). These infrastructures and environments are depicted diagrammatically in the figure below.
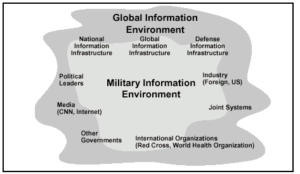
Information Infrastructures and Environments
Information Superiority
The central objective of IW is achievement of information superiority.
Definition
Information superiority is the ability to collect, process and disseminate an uninterrupted flow of information while denying an adversary’s capability to do the same. It is that degree of dominance in the information domain that permits the conduct of operations without effective opposition.
Principles of Information Superiority
These are as under [3]:-
- Dominant Manoeuvre. Information superiority allows agile organisations with high-mobility weapons to attack rapidly at an aggressor’s centres of gravity across the full depth of the battlefield. Synchronised and sustained attacks are achieved by dispersed forces, integrated by an information grid.
- Precision Engagement. Near real-time information on targets provides the ability to engage and reengage targets with spatial and temporal precision (“at the right place, just at the right time”).
- Focused Logistics. Information superiority enables efficient delivery of sustenance packages in the battlefield, optimising the logistics process.
- Full-Dimension Protection. Protection of forces is achieved only if superior information provides continuous threat vigilance, and in turn provides freedom of offensive action.
Achieving Information Superiority
The process by which information superiority is achieved is depicted in the figure which follows [4]. The figure illustrates that the result of information superiority is to integrate its four operating principles to obtain the military objective of achieving massed effects (as against massed forces) of force application. The two contributing components of information superiority are as under:-
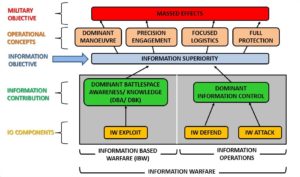
Achieving Information Superiority
- Dominant Battlespace Awareness/ Knowledge (DBA/ DBK). The comprehensive awareness of all the decision-relevant elements within a defined battlespace, and the ability to predict with very high confidence near-term enemy actions and combat outcomes – achieved through the IW Exploit function.
- Information Operations. Actions taken to affect adversary information and information systems while defending one’s own information and information systems – captured under the paradigm of Dominant Information Control (IW Attack and Defend functions).
The figure also makes a distinction between Information-Based Warfare (IBW), which is the use of information to wage war (essentially applied DBA/DBK), and IW, a more comprehensive term which in addition includes and primarily implies the targeting and defending of information itself (Information Operations (IO)), using information weapons, amongst others.
DBA/ DBK vis-à-vis Intelligence, Surveillance and Reconnaissance (ISR)
The IW Exploit function leads to DBA/ DBK primarily through the medium of ISR (although the IW Exploit sub-function of the IW Attack component also contributes towards DBA/ DBK).
Also of relevance is the fact that ISR targets are mostly non-information entities with the end result being information. This is presumably the reason why it has been excluded from the scope of IO as depicted above.
Importance of Definitions
Martin Libicki [4] has the following to say on the importance of good definitions: “Clarifying the issues is more than academic quibbling. First, (if not defined properly) one aspect of IW, perhaps championed by a single constituency, assumes the role of an entire concept, thus becoming grossly inflated in importance. Second, too broad a definition makes it impossible to discover any common conceptual thread other than the obvious (that information warfare involves ‘information’ and ‘warfare’) where a tighter definition might reveal one.” Against this backdrop, the following points merit mention:-
- A common (universally accepted) perspective on IW/ IO does not as yet exist. The US DOD definition of IO itself has undergone at least several revisions over the last decade and a half.
- Definitions of core concepts are central to the manner in which they unfold into an operational philosophy.
IW vis-à-vis IO
The terms IW and IO are often used synonymously. The following discussion throws light on their relationship:-
- As depicted in the figure above, IO is that subset of IW which leads to Dominant Information Control (IW Attack and Defend functions) but excludes DBA/ DBK (IW Exploit function).
- Another relationship emerges from usage of these terms in US doctrine. Initially, US IW doctrine was written in terms of Command and Control Warfare (C2W) [5]. The term IO replaced IW in 1996, while the term C2W was dropped from US doctrine in 2006. Both C2W and IO imply application of IW in the military context. However, IO has a broader scope, in that while C2W is limited to the crises/ conflict stages, IO covers activities (including defensive preparations) carried out during peace also [6]. In other words, IO denotes application of IW in the military context, applied throughout the peace – crises – conflict continuum.
- An analysis of the US IO Doctrine also indicates that the DBA/ DBK component has been excluded from the scope of IO (ie, ISR is not an IO capability), in line with the above figure depicting the model for achieving information superiority.
IW vis-à-vis Network Centric Warfare (NCW)
The NCW concept is captured in its tenets, depicted diagrammatically in the following figure [7] and briefly explained below (a more detailed discussion is available in two earlier posts on Network Centric Warfare: Origins and Main Characteristics and Network Centric Warfare: Understanding the Concept):-
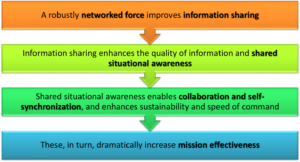
- NCW is considered to be a paradigm shift in war fighting methods, entailing a change in strategy from trying to concentrate “massed forces” to achieving “massed effects” by developing and leveraging DBA/ DBK.
- With DII as a prerequisite, it envisages use of sensor netting, data fusion and information management techniques to create shared battlespace awareness. Thereafter, using virtual organisations and self-synchronisation of forces, it achieves increased responsiveness, agility, tempo of operations and finally increased combat effectiveness.
- It is pointed out here that except for the sensor element which integrates to the adversary battlespace (mostly to the physical domain and partially to the information domain) the balance of the play of NCW is in one’s own infosphere.
The following may be stated on the relationship between IW and NCW:-
- Both IW and NCW are indeed information age concepts. However, the commonality ends there. While IW is a struggle in the information domain to achieve dominant information control (attack/ defend functions), NCW leverages DBA/ DBK (exploit function) to achieve increased combat efficiency primarily in the physical domain.
- Though there is a weak relation between these two concepts in the information domain, NCW clearly does not form an element of IW, nor vice versa.
In summary, NCW and IO are two important complementary concepts, both of which appear to have significant potential for being operationalised and taken advantage of in 21st Century warfare.
The Indian Security Scenario – Overview of IW Status
Indian Joint and Army IW Doctrines
Both the Joint IW Doctrine and Indian Army IW Doctrine 2004 enunciate elements/ forms of IW in line with Libicki’s IW taxonomy (discussed above). In addition, the doctrines also list NCW and Space Warfare as elements of IW [8]. The following comments can be made on this aspect:-
- On analysis it is seen that Libicki’s taxonomy is unsuited as a basis for military IO doctrine, for the following reasons: In Libicki’s own words, the seven forms are “weakly related” and lack “analytical coherence”; the disciplines are not restricted to the military domain (eg, EIW); some of the disciplines are not amenable to being operationalised but have a broad scope involving several functions (C2W, EIW, IBW); and finally, the disciplines have overlapping components (for instance, EW may be used as part of C2W, in support of IBW or simply as EW).
- The latest IA IW Doctrine focusses on three capabilities, ie, EW, Cyber W and Psy Ops [9]. While these are indeed the three most important components in our context, some significant elements of IO which have been left out also need to be included, eg, Military Deception, Public Affairs/ Information, Physical Attack, etc.
- The terms IW and IO are used synonymously in all Indian doctrinal literature, and it is felt that these terms need to be disambiguated. Also, lack of a well-structured operational definition is a hindrance towards understanding the concept of IW/ IO and its application in the Indian context, as also the responsibilities of staff and line directorates.
- In general, the increasing importance of IO in current times dictates a more focussed treatment of doctrinal issues.
IW Capabilities
The IW capabilities of the IA got its first major impetus in the 1980s, with the induction of the first few EW systems from Hungary. Thereafter, indigenous integrated EW systems were developed by Defence Research and Development Organisation (DRDO) under Project Samyukta. A number of other discrete and integrated EW systems have been procured as well as indigenously developed over the years. Similarly, cyber capabilities, both defensive and offensive, are continuously being upgraded at the strategic, operational and tactical levels. The discipline of perception management has matured over time especially in the context of counter-insurgency operations. Organisational upgradations have been effected, both in terms of staff appointments and field units.
There appears to be a clear need, however, to assess the capabilities being acquired by major world militaries, including potential adversaries, and accord due importance to this new dimension of warfare which has emerged in 21st Century warfare.
References
(1) John Arquilla and David Ronfeldt, Cyberwar is Coming! Comparative Strategy, Vol 12, No. 2, Spring 1993, pp. 141–165, Accessed 31 Aug 2020, https://www.rand.org/pubs/reprints/RP223.html.
(2) Martin Libicki, What is Information Warfare? US National Defence University ACIS Paper 3, Aug 1995, Preface p. 1, Accessed 31 Aug 2020, http://www.iwar.org.uk/iwar/resources/ndu/infowar/a003cont.html.
(3) Edward Waltz, Information Warfare: Principles and Operations, Artech House, Inc., Norwood, 1998, pp. 173-174, pp. 108-109, pp. 109-110, Accessed 31 Aug 2020, https://www.amazon.com/Information-Warfare-Principles-Operations-Computer/dp/089006511X.
(4) Martin Libicki, What is Information Warfare? US National Defence University ACIS Paper 3, Aug 1995, Chapter 1 p. 2.
(5) US DOD Jt Pub 3-13.1, Joint Doctrine for Command and Control Warfare (C2W), 07 Feb 1996, Accessed 31 Aug 2020, https://www.bits.de/NRANEU/others/jp-doctrine/jp3_13_1.pdf.
(6) Gregory J Rattray, Strategic Warfare in Cyberspace, The MIT Press, Massachusetts, 2001, p. 328, Accessed 31 Aug 2020, https://mitpress.mit.edu/books/strategic-warfare-cyberspace.
(7) David S. Alberts, John J. Garstka, and Frederick P. Stein, Network Centric Warfare: Developing and Leveraging Information Superiority, Washington, DC: CCRP Publication Series, 1999, p. 89, Accessed 31 Aug 2020, http://dodccrp.org/files/Alberts_NCW.pdf.
(8) Panwar, Brig R S, Information Warfare: Implementation Approach for the IA, Dissertation, National Defence College, 2008, p. 37.
(9) Panwar, Brig R S, Information Operations: Concepts and Way Forward, The Army War College Journal, Summer 2016, ISSN 2394-5613, pp. 36-43.


0 Comments