THE CHANGING NATURE OF WARFARE - PART II
Sections
Background
Some Modern Warfighting Concepts
Information Age Warfighting Concepts
The Indian Security Scenario
References
Background
Over the centuries, warfare has undergone significant transformation, due to new discoveries and innovative application of technologies. These inventions and discoveries have resulted in dramatic changes in military doctrine as well as operational and organisational concepts, and have altered the character and conduct of military operations.
Part I of this write-up covered discussed the changing nature of warfare over the last several centuries, based on Lind’s categorisation of “Generations of Warfare” as well as the concept of “Revolution in Military Affairs” (RMA). This part looks at the fast changing pace at which warfighting concepts are undergoing change, especially as a result of rapid technological advancements in this Information Age.
In present times, we are witnessing a wide spectrum of conflicts across the global arena. While one may attempt to classify these as extrapolations of the concepts of “generations of warfare” and “RMAs”, various authors have come up with new terminologies such as “Asymmetric Warfare”, “Unrestricted Warfare”, “Hybrid Warfare”, “Colour Revolutions”, etc, to capture their flavour. It is evident, however, that the spectacular advancements being made in a wide variety of technologies, especially information and communication technologies (ICT), have had a significant impact on warfare in all its flavours. Furthermore, new Information Age warfighting concepts have emerged, such as “Network Centric Warfare”, “Information Warfare”, “Cyber Warfare”, etc.
Let us take a brief look at some of the aspects listed above.
Some Modern Warfighting Concepts
Asymmetric Warfare
Some technologists made an assumption that the RMA brought about by the Information Age would favour technologically advanced nations and failed to consider how enemies with asymmetric strategies might conduct war in this Age. The gap between the haves and have-nots has led to the emergence of a different form of warfare known as “asymmetric warfare”, which involves parties with disparate military capabilities and strategies. This disparity has resulted in unconventional warfare tactics, wherein the weaker combatants exploit the weaknesses of the adversary, while offsetting their deficiencies in quantity or quality. Events such as the Vietnam War, Iraq War, 9/11, Afghan War, ISIS operations, etc, have amply demonstrated that adversaries have adapted to the capabilities of technological advanced armies, by adopting asymmetric responses to their advantage [1].
Unrestricted Warfare
In 1999, two Chinese PLA Colonels, Qiao Liang and Wang Xiangtsui, came up with their conception of “Unrestricted Warfare”, or “war beyond limits.” They proposed the idea that “warfare is no longer an activity confined only to the military sphere,” and must include information warfare, financial warfare, trade warfare and other entirely new forms of war. They stated that adversaries, in this age, would attempt to employ all the dimensions of warfare asymmetrically to counter critical military capabilities in such areas as conventional warfare, force projection, C4ISR (including space operations) and precision strike [2].
Hybrid Warfare
The term “hybrid threat” was coined to characterize the increased complexity and nonlinearity of threat actors. A “hybrid threat” may be defined as an adversary, state or non-state actor that adaptively and rapidly incorporates diverse and dynamic combinations of conventional, irregular, asymmetric and criminal capabilities, as well as non-military means, simultaneously across the spectrum of conflict as a unified force to obtain its objectives. “Hybrid Wars” blend the lethality of state conflict with the fanatical and protracted fervour of irregular warfare. A detailed analysis of hybrid warfare is given in The Challenges of Hybrid Warfare [3].
Colour Revolutions
Colour Revolutions refer to the string of protests, uprisings, and government overthrows in the former Soviet Union, Middle East, North Africa and Asia that have churned things up in the 21st Century. Notable examples include the 2003 Rose Revolution in Georgia and the 2004 Orange Revolution in Ukraine, as well as the Arab Spring. The common features of Colour Revolutions involve replacement of more restrictive governments with more liberal, more legitimate governments through peaceful, popular protest. According to a Defence News article [4], Colour Revolutions were developed by the US and its allies “to destabilize governments and replace existing regimes in order to establish control and exploit natural resources.” Some observers are calling this mode of conflict 5th Generation War (5GW), though this term does not have wide acceptance. Others call it 4th Generation, 6th Generation, and very occasionally, 7th Generation Warfare. All of which shows that counting can be a real puzzler to military theorists!
Information Age Warfighting Concepts
General
Against the backdrop of the generational shifts in warfare and the concept of RMAs, including the current “systems of systems”, we shall now briefly discuss some warfighting concepts which have emerged with the maturing of the Information Age. These are Information Warfare, Cyberspace Operations and Network Centric Warfare.
Information Warfare (IW)/ Information Operations (IO)
Most of the doctrinal concepts on IW and IO have emerged from the US and thereafter adopted by other countries. A brief overview of doctrines of the US and India is given out in succeeding paragraphs.
- US. Although the terms IW and IO are used synonymously by some, a close analysis of US doctrine shows that, from the US perspective, IO denotes application of IW in the military context, applied throughout the peace – crises – conflict continuum. US DoD has a joint doctrine for IO, not for IW. The latest revision of US DoD Doctrine, issued in Jun 2014, characterizes IO as the integrated employment, during military operations, of Information Related Capabilities (IRCs) in concert with other lines of operation to influence, disrupt, corrupt, or usurp the decision making of adversaries and potential adversaries while protecting our own.” The doctrine lists 14 IRCs, while stating that there could be more, emphasizing that it is not individual capabilities that are important but rather the use of those as force multipliers to create the desired effect. The IRCs listed are: Strategic Communication, Joint Interagency Coordination, Public Affairs, Civil-Military Operations, Cyberspace Operations, Information Assurance, Space Operations, Military Information Support Operations (MISO), Intelligence, Military Deception, Operational Security, Special Technical Operations, Joint Electromagnetic Spectrum Operations and Key Leadership Engagement [5].
- India. The Joint IW Doctrine of the Indian Defence Forces as well as the IW Doctrine for the IA define IW on the lines of earlier versions of IW/ IO definitions given out in US IW/ IO doctrines [6]. It is noteworthy, however, that the terminology used by the IA in the military context is IW and not IO. Further, the latest IA IW doctrine focusses primarily on three components of IW, namely, Electronic Warfare, Cyber Warfare and Psychological Warfare.
- Other World Militaries. Taking a cue from the US, China, NATO, UK, Canada and several other countries have evolved their doctrines on IO [7], [8], [9].
- Information Superiority. The central objective of IW/ IO is achievement of information superiority [10], which is defined as “the ability to collect, process and disseminate an uninterrupted flow of information while denying an adversary’s capability to do the same. It is that degree of dominance in the information domain that permits the conduct of operations without effective opposition.” Its four main principles are stated to be Dominant Manoeuvre, Precision Engagement, Focused Logistics and Full-Dimension Protection.
Cyberspace Operations
The US is probably the only country to have formulated a full-fledged doctrine on Cyberspace Operations (CO). As per this doctrine, CO are the employment of cyberspace capabilities where the primary purpose is to achieve objectives in or through cyberspace. CO are composed of the military, intelligence, and ordinary business operations in cyberspace. The successful execution of CO requires integrated Offensive, Defensive and Information Network Operations, as under [11]:-
- Offensive Cyberspace Operations. These are CO intended to project power by the application of force in and through cyberspace.
- Defensive Cyberspace Operations. These are CO intended to defend DoD or other friendly cyberspace. Specifically, they are passive and active cyberspace defence operations to preserve the ability to utilize friendly cyberspace capabilities and protect data, networks, net-centric capabilities, and other designated systems.
- Information Network Operations. These are actions taken to design, build, configure, secure, operate, maintain, and sustain communications systems and networks in a way that creates and preserves data availability, integrity, confidentiality, as well as user/ entity authentication and non-repudiation.

Cyberspace – A Warfighting Domain
The Relationship between IO and CO
CO are concerned with using cyberspace capabilities to create effects which support operations across the physical domains and cyberspace. Thus, cyberspace is a medium through which IRCs, such as MISO or military deception, may be employed. However, IO also uses capabilities from the physical domains for its objectives. While some CO may support IO objectives, other CO will be conducted in support of target objectives, or to support operations in the physical domains to achieve objectives. This relationship represents an evolution both in IO, transitioning from a collection of capabilities to a broader integrating function focused on the adversary, and in CO, evolving from its computer network operations roots into a way to operationally integrate CO within joint operations [9]. In the past, CO have been considered a subset of IO and those operations incorporated in the terms Computer Network Operations (CNO), Computer Network Attack (CNA), Computer Network Defence (CND) and Computer Network Exploit (CNE). These terminologies are still in use by many armies, including the IA. Figure 1.2a depicts the inter se relationship between IO and CO.
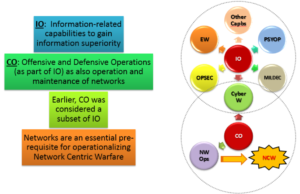
Relationship between IO and CO
Network Centric Warfare
NCW is an emerging theory of war in the Information Age. It is also a concept that, at the highest level, constitutes the military’s response to the Information Age. The term “network centric warfare”, first coined by Vice Admiral Arthur K Cebrowski, US Navy, broadly describes the combination of strategies, emerging tactics, techniques and procedures, as well as organizations that a fully or even a partially networked force can employ to create a decisive warfighting advantage. Although the NCW concept requires a separate treatment to be understood adequately, its main themes are listed here, as under [12]:-
- NCW generates increased combat power by networking sensors, decision makers and shooters to achieve shared awareness, increased speed of command, high tempo of operations, greater lethality, increased survivability, and a degree of self-synchronization.
- It enables move of combat power from the linear battlespace to non-contiguous operations by emphasizing functional control instead of physical occupation of the battlespace, in order to generate effective combat power at the proper time and place.
- It moves away from an approach based on geographically contiguous massing of forces to one based upon massing of effects, thus limiting the need to mass physical forces within a specific geographical location.
- NCW theory has applicability at all three levels of warfare – strategic, operational, and tactical – and across the full range of military operations from major combat operations to stability and peacekeeping operations.
- The implementation of NCW is first of all about human behavior as opposed to information technology. While “network” is a noun, “to network” is a verb. Thus, when we examine the degree to which a particular military organization is exploiting the power of NCW, our focus should be on human behavior in the networked environment.
The Indian Security Scenario
The concepts of “asymmetric warfare”, “unrestricted warfare” and “hybrid warfare” are all very relevant in the Indian Security Scenario. The current adversarial relationship between India and Pakistan is a good example of hybrid warfare, having conventional, sub-conventional and nuclear military dimensions on the one hand, as also the use of political and economic means to achieve the desired end result on the other.
As is true with almost all global conflicts in present times, India is equally vulnerable to information operations and, in particular, cyber warfare. India’s own efforts to achieve offensive capabilities in these warfighting domains have been ongoing for over two decades now. It has acquired significant electronic warfare (EW) capabilities, has cyber organisations in place, and recognises the need to hone its psychological operations (Psy Ops) capabilities. The Indian Army (IA) warfighting doctrines recognise the importance of NCW, and many initiatives have been taken over the years to achieve net-centric capabilities. However, the pace of these efforts clearly needs to be accelerated.
This concludes this two-part write-up, which has attempted to give an overview of the manner in which warfighting concepts have undergone a change over the last several centuries and, more importantly, how the metamorphosis in the nature of warfare in the 21st Century is occurring at a breath-taking pace, making it difficult for even the advanced armies to keep pace with the ever evolving complexities of present-day conflicts and maintain their winning edge.
References
(1) Buffaloe D L, Defining Asymmetric Warfare, The Land Warfare Papers, The Institute of Land Warfare, Virginia, USA, September 2006.
(2) Qiao Liang and Wang Xiangsui, Unrestricted Warfare, PLA Literature and Arts Publishing House, Beijing, Feb 1999.
(3) Eve Hunter and Piret Pernik, The Challenges of Hybrid Warfare, International Centre for Defence and Security, Talinn, Estonia, April 2015.
(4) Faith R, Fifth Generation Warfare: Taste the Color Revolution Rainbow, Vice News, War and Conflict Section, 06 Jun 2014, Available: [Online: https://news.vice.com /article/ fifth-generation-warfare-taste-the-color-revolution-rainbow].
(5) Information Operations, Joint Publication 3-13, US DoD, 27 Nov 12, Incorporating Change 1, 20 Nov 14.
(6) Panwar, Brig R S, Information Warfare: Implementation Approach for the IA, Dissertation, National Defence College, 2008.
(7) Kanwal G, China’s Emerging Cyber War Doctrine, Journal of Defence Studies, Vol 3, No 3, Jul 2009, pp. 15-20.
(8) Allied Joint Publication 3.10, Allied Joint Doctrine for Information Operations, 11 Feb 2019.
(9) Neil Chuka, A Comparison of the Information Operations Doctrine of Canada, the United States, the United Kingdom, and NATO, Canadian Army Journal, Vol 12.2, 2009.
(10) Waltz, Edward, Information Warfare: Principles and Operations, Artech House, Inc, Norwood, 1998, pp. 27, 51, 108-110, 173-174.
(11) US Joint Chiefs of Staff, Cyberspace Operations, US DoD Joint Publication 3-12 (R), 05 Feb 13, pp. I-2, I-5-I-6, II-1, II-2.
(12) Cebrowski A K, The Implementation of Network Centric Warfare, Office of Force Transformation, US DoD, Washington, D C, 05 Jan 2005, pp. 15-21.


0 Comments